Researchers have discovered malicious code circulating in the wild that hijacks the earliest stage boot process of Linux devices by exploiting a year-old firmware vulnerability when it remains unpatched on affected models.
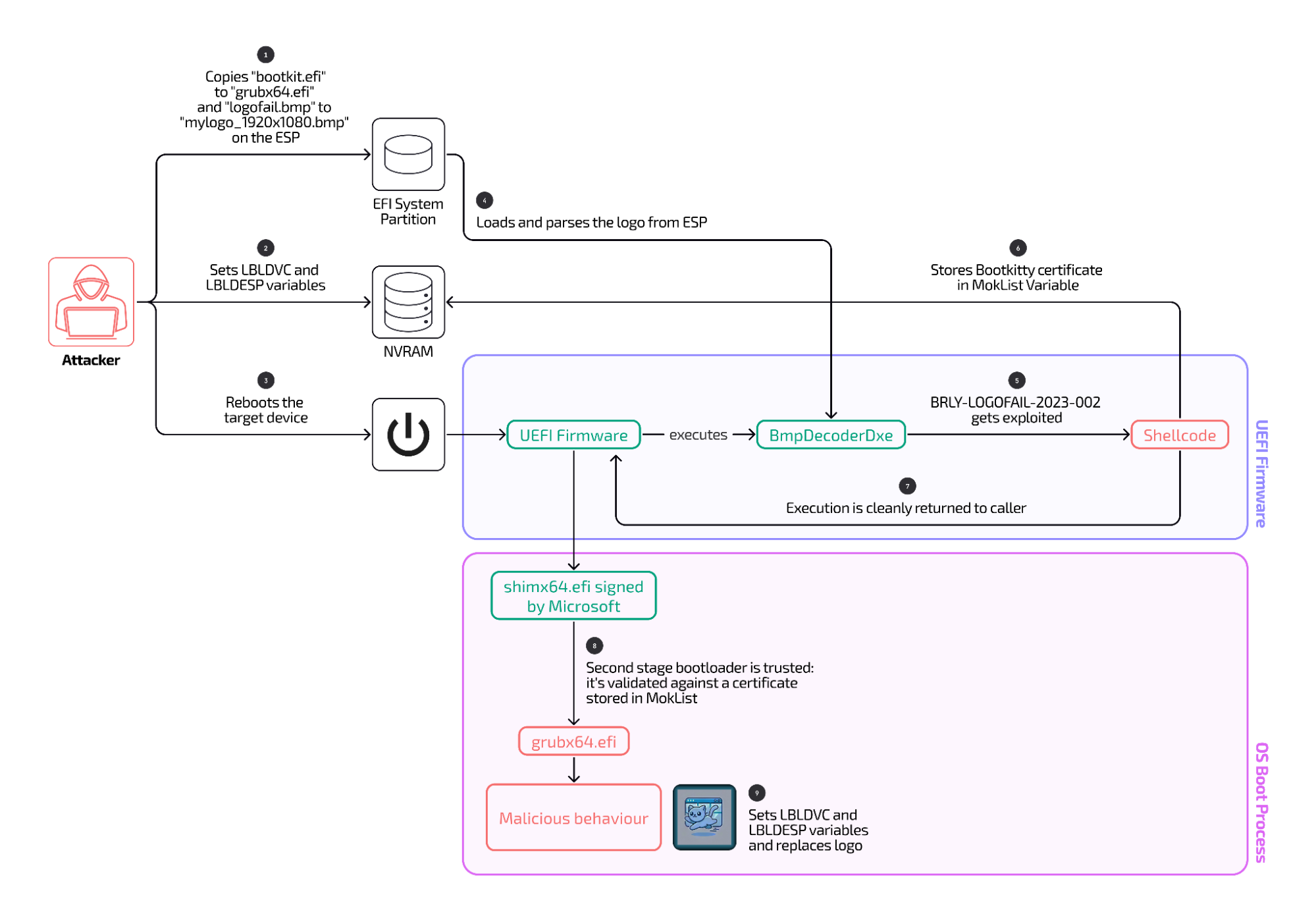
The critical vulnerability is one of a constellation of exploitable flaws discovered last year and given the name LogoFAIL. These exploits are able to override an industry-standard defense known as Secure Boot and execute malicious firmware early in the boot process. Until now, there were no public indications that LogoFAIL exploits were circulating in the wild.
The discovery of code downloaded from an Internet-connected web server changes all that. While there are no indications the public exploit is actively being used, it is reliable and polished enough to be production-ready and could pose a threat in the real world in the coming weeks or months. Both the LogoFAIL vulnerabilities and the exploit found on-line were discovered by Binarly, a firm that helps customers identify and secure vulnerable firmware.
Theoretical no more
“LogoFAIL was a theoretical vulnerability, and the PoC was not weaponized,” Binarly founder and CEO Alex Matrosov wrote in an interview, referring to the proof-of-concept code released by Binarly as part of the company's earlier disclosure. “This discovery shows the issues, which are hard to fix around the ecosystem, could be exploited in the wild and weaponized. The funny part is it's almost a year since we disclosed it publicly, and this happens now when threat actors have adopted it.”
The ultimate objective of the exploit, which Binarly disclosed Friday, is to install Bootkitty, a bootkit for Linux that was found and reported on Wednesday by researchers from security firm ESET. Binarly said the exploit the company uncovered injects code into the UEFI, the firmware responsible for booting modern devices that run Windows or Linux. It does this by exploiting one of about a dozen critical image-parsing bugs that comprise the LogoFAIL constellation.




 Loading comments...
Loading comments...
